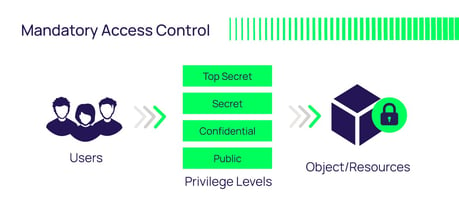
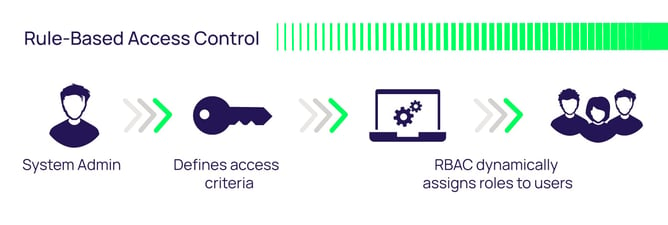
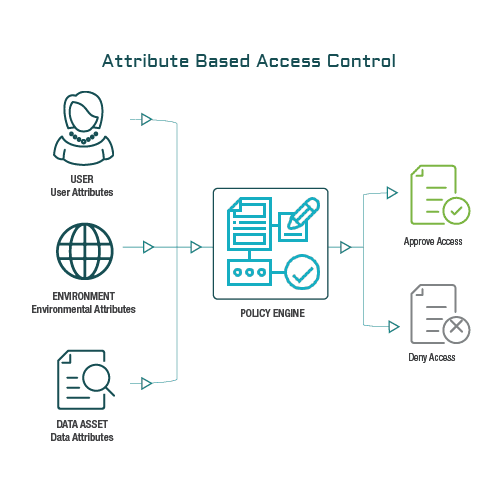
Discretionary and Non-Discretionary Access Control Policies by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

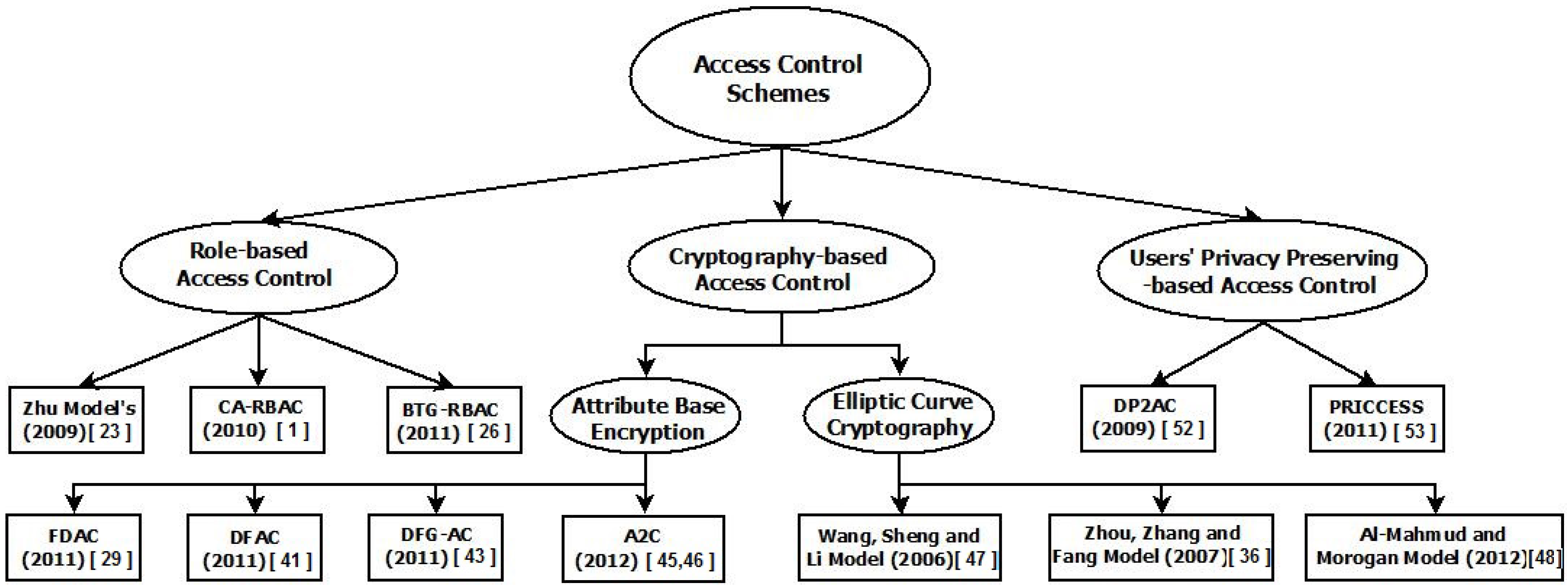
A survey on access control mechanisms for cloud computing - El Sibai - 2020 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library




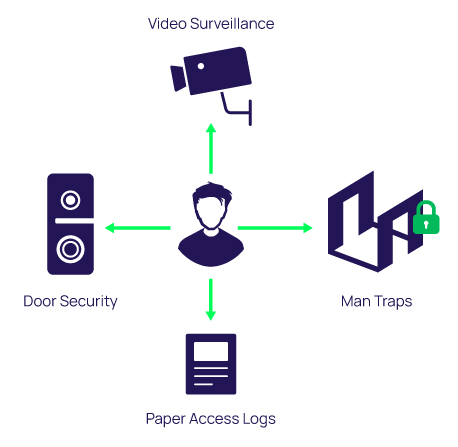




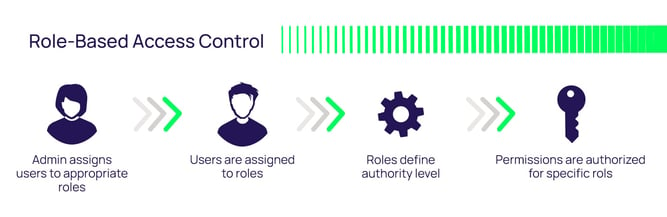
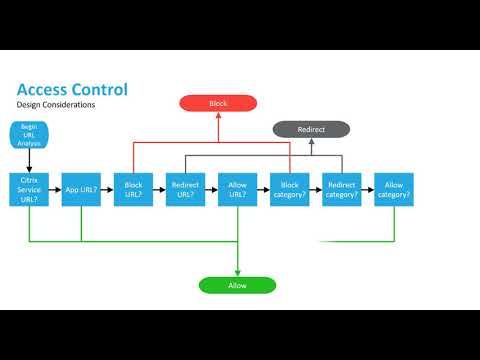


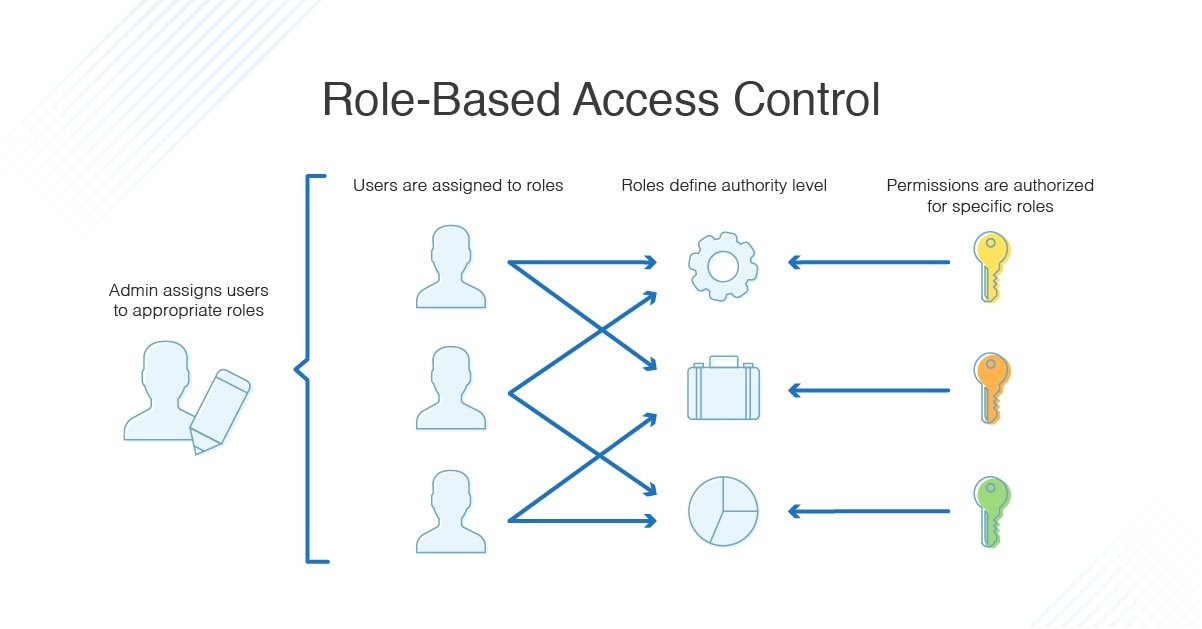
![1: Lampson's access-control model.[21] | Download Scientific Diagram 1: Lampson's access-control model.[21] | Download Scientific Diagram](https://www.researchgate.net/publication/228728499/figure/fig1/AS:650845624475656@1532185097309/Lampsons-access-control-model21.png)