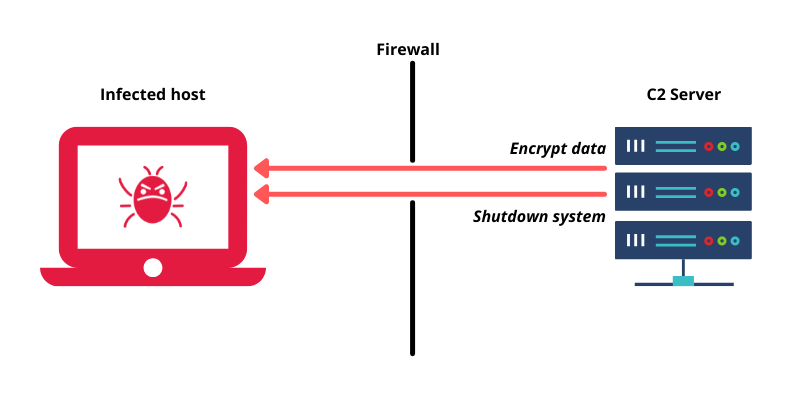
Information | Free Full-Text | A Botnets Circumspection: The Current Threat Landscape, and What We Know So Far
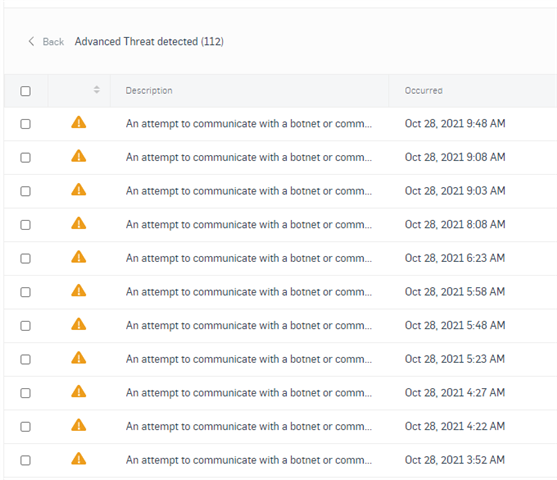
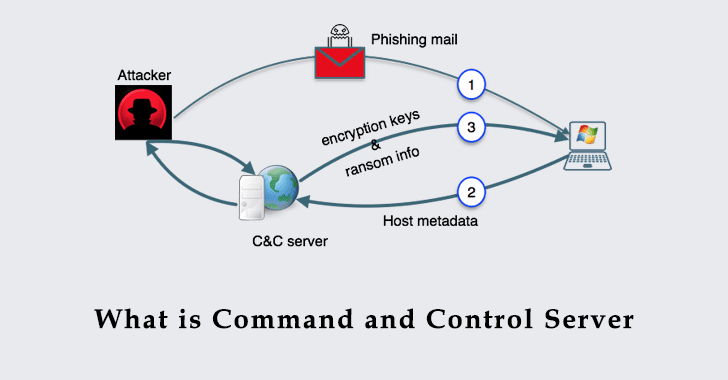
An attempt to communicate with a botnet or command and control server has been detected - Network Protection: Firewall, NAT, QoS, & IPS - UTM Firewall - Sophos Community
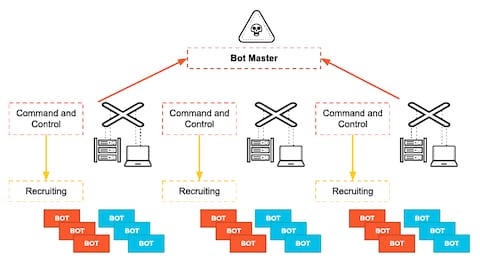
![PDF] A Survey of Botnet Detection Techniques by Command and Control Infrastructure | Semantic Scholar PDF] A Survey of Botnet Detection Techniques by Command and Control Infrastructure | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b00172784a7dbb611f06329c66ab9e10a1c07f35/7-Figure2-1.png)
PDF] A Survey of Botnet Detection Techniques by Command and Control Infrastructure | Semantic Scholar
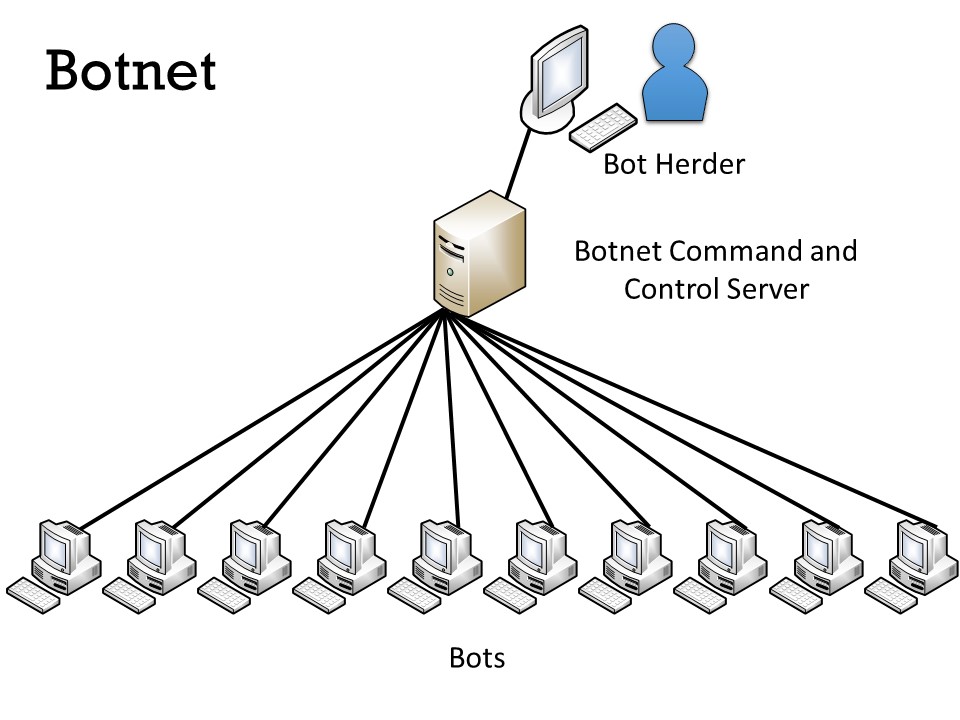
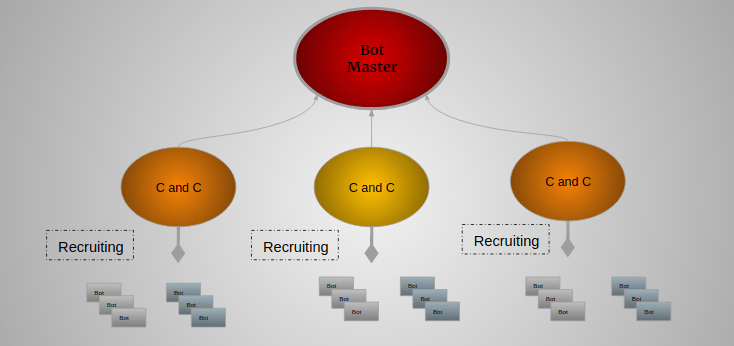
Basic entities of botnet: bots, command and control (C&C) server, and... | Download Scientific Diagram
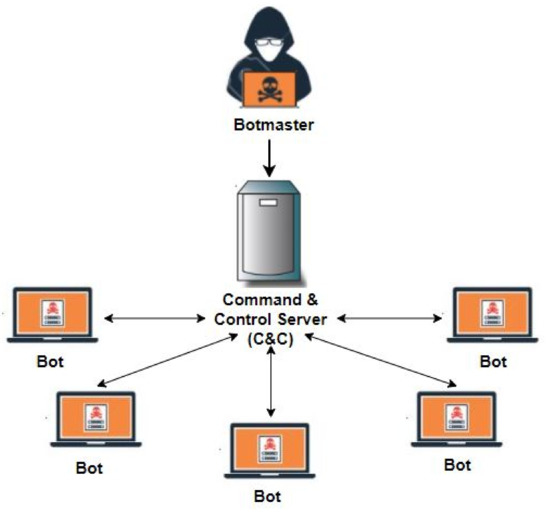
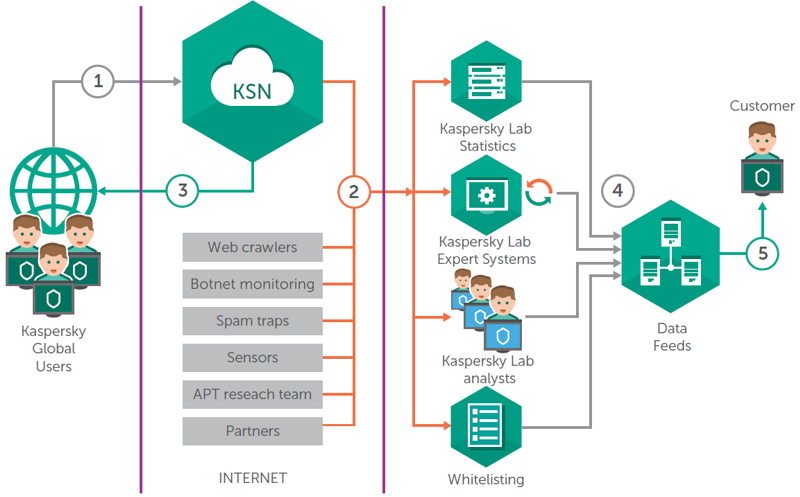
Symmetry | Free Full-Text | Machine Learning-Based Botnet Detection in Software-Defined Network: A Systematic Review