Command and Control (C2) to enable multi-domain teaming of unmanned vehicles (UxVs) | Semantic Scholar

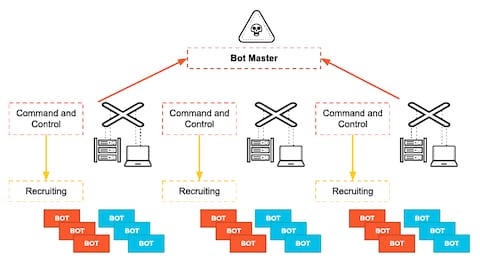
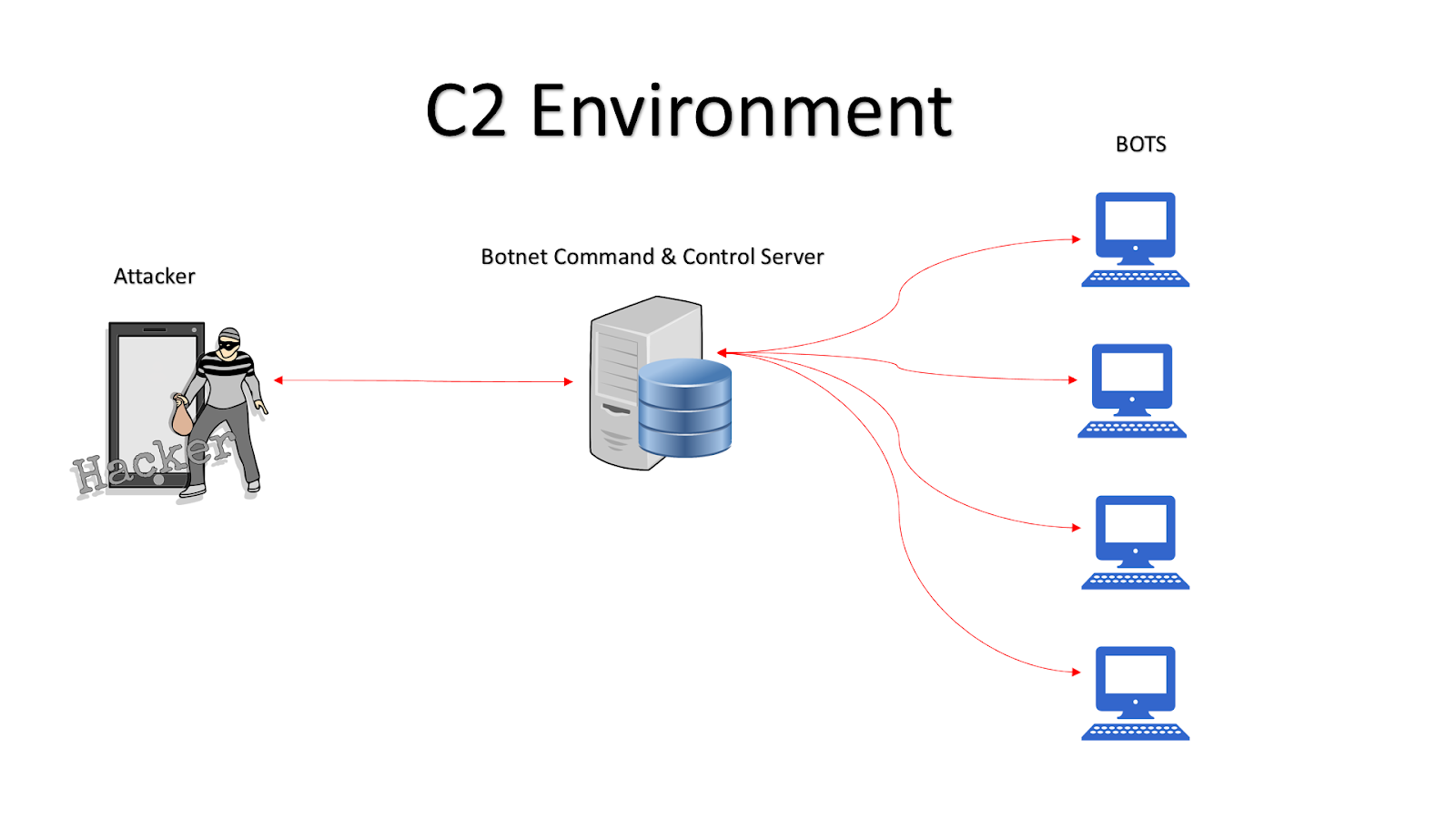
The command and control (C2) component controls the resources in the... | Download Scientific Diagram

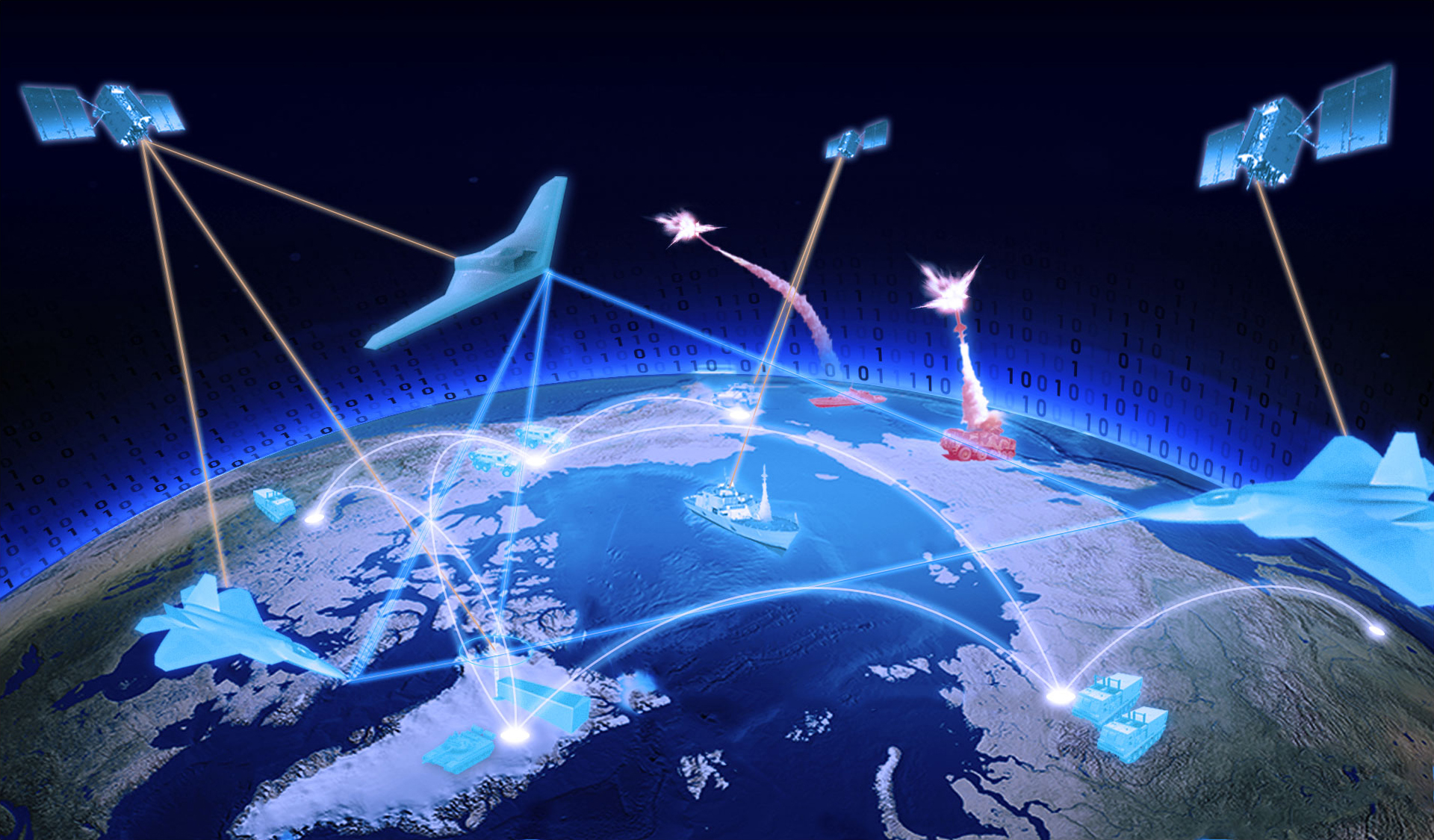
This experimental Command and Control (C2) architecture incorporates... | Download Scientific Diagram